Good morning, everyone!
之前我们已经说过用Shiro和JWT来实现身份认证和用户授权,今天我们再来说一下Security和JWT的组合拳。
简介
先赘述一下身份认证和用户授权:
- 用户认证(
Authentication):系统通过校验用户提供的用户名和密码来验证该用户是否为系统中的合法主体,即是否可以访问该系统; - 用户授权(
Authorization):系统为用户分配不同的角色,以获取对应的权限,即验证该用户是否有权限执行该操作;
Web应用的安全性包括用户认证和用户授权两个部分,而Spring Security(以下简称Security)基于Spring框架,正好可以完整解决该问题。
它的真正强大之处在于它可以轻松扩展以满足自定义要求。
原理
Security可以看做是由一组filter过滤器链组成的权限认证。它的整个工作流程如下所示: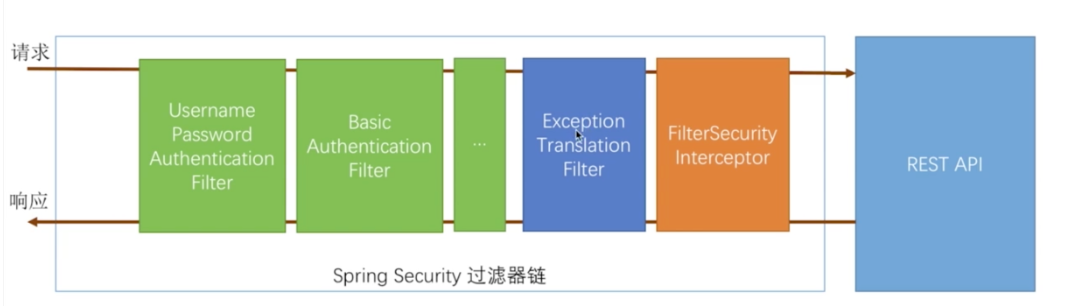
图中绿色认证方式是可以配置的,橘黄色和蓝色的位置不可更改:
FilterSecurityInterceptor:最后的过滤器,它会决定当前的请求可不可以访问ControllerExceptionTranslationFilter:异常过滤器,接收到异常消息时会引导用户进行认证;
实战
项目准备
我们使用Spring Boot框架来集成。
1.pom文件引入的依赖
<dependency> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter</artifactid></dependency><dependency> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter-web</artifactid> <exclusions> <exclusion> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter-tomcat</artifactid> </exclusion> </exclusions></dependency><dependency> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter-undertow</artifactid></dependency><dependency> <groupid>mysql</groupid> <artifactid>mysql-connector-java</artifactid></dependency><dependency> <groupid>com.baomidou</groupid> <artifactid>mybatis-plus-boot-starter</artifactid> <version>3.4.0</version></dependency><dependency> <groupid>org.projectlombok</groupid> <artifactid>lombok</artifactid></dependency><!-- 阿里JSON解析器 --><dependency> <groupid>com.alibaba</groupid> <artifactid>fastjson</artifactid> <version>1.2.74</version></dependency><dependency> <groupid>joda-time</groupid> <artifactid>joda-time</artifactid> <version>2.10.6</version></dependency><dependency> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter-test</artifactid></dependency>2.application.yml配置
spring: application: name: securityjwt datasource: driver-class-name: com.mysql.cj.jdbc.Driver url: jdbc:mysql://127.0.0.1:3306/cheetah?characterEncoding=utf-8&useSSL=false&serverTimezone=UTC username: root password: 123456server: port: 8080mybatis: mapper-locations: classpath:mapper/*.3.SQL文件
/*** sys_user_info**/SET NAMES utf8mb4;SET FOREIGN_KEY_CHECKS = 0;-- ------------------------------ Table structure for sys_user_info-- ----------------------------DROP TABLE IF EXISTS `sys_user_info`;CREATE TABLE `sys_user_info` ( `id` bigint(20) NOT NULL AUTO_INCREMENT, `username` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL, `password` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL, PRIMARY KEY (`id`) USING BTREE) ENGINE = InnoDB AUTO_INCREMENT = 3 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;SET FOREIGN_KEY_CHECKS = 1;/*** product_info**/SET NAMES utf8mb4;SET FOREIGN_KEY_CHECKS = 0;-- ------------------------------ Table structure for product_info-- ----------------------------DROP TABLE IF EXISTS `product_info`;CREATE TABLE `product_info` ( `id` bigint(20) NOT NULL AUTO_INCREMENT, `name` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL, `price` decimal(10, 4) NULL DEFAULT NULL, `create_date` datetime(0) NULL DEFAULT NULL, `update_date` datetime(0) NULL DEFAULT NULL, PRIMARY KEY (`id`) USING BTREE) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;SET FOREIGN_KEY_CHECKS = 1;引入依赖
<dependency> <groupid>org.springframework.boot</groupid> <artifactid>spring-boot-starter-security</artifactid></dependency><!--Token生成与解析--><dependency> <groupid>io.jsonwebtoken</groupid> <artifactid>jjwt</artifactid> <version>0.9.1</version></dependency>引入之后启动项目,会有如图所示: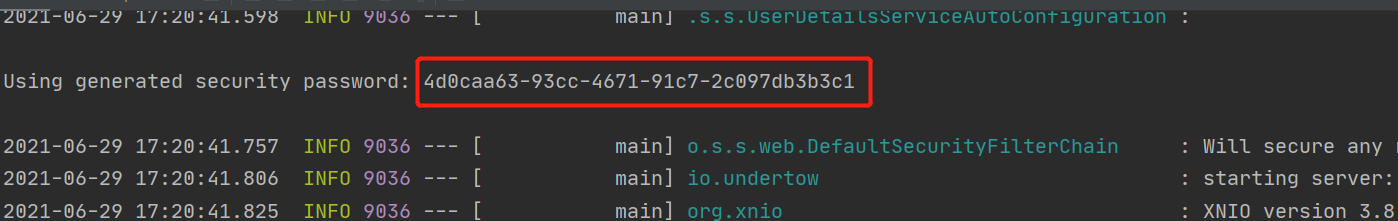
其中用户名为user,密码为上图中的字符串。
SecurityConfig类
//开启全局方法安全性@EnableGlobalMethodSecurity(prePostEnabled=true, securedEnabled=true)public class SecurityConfig extends WebSecurityConfigurerAdapter { //认证失败处理类 @Autowired private AuthenticationEntryPointImpl unauthorizedHandler; //提供公钥私钥的配置类 @Autowired private RsaKeyProperties prop; @Autowired private UserInfoService userInfoService; @Override protected void configure(HttpSecurity httpSecurity) throws Exception { httpSecurity // CSRF禁用,因为不使用session .csrf().disable() // 认证失败处理类 .exceptionHandling().authenticationEntryPoint(unauthorizedHandler).and() // 基于token,所以不需要session .sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS).and() // 过滤请求 .authorizeRequests() .antMatchers( HttpMethod.GET, "/*.html", "/**/*.html", "/**/*.css", "/**/*.js" ).permitAll() // 除上面外的所有请求全部需要鉴权认证 .anyRequest().authenticated() .and() .headers().frameOptions().disable(); // 添加JWT filter httpSecurity.addFilter(new TokenLoginFilter(super.authenticationManager(), prop)) .addFilter(new TokenVerifyFilter(super.authenticationManager(), prop)); } //指定认证对象的来源 public void configure(AuthenticationManagerBuilder auth) throws Exception { auth.userDetailsService(userInfoService) //从前端传递过来的密码就会被加密,所以从数据库 //查询到的密码必须是经过加密的,而这个过程都是 //在用户注册的时候进行加密的。 .passwordEncoder(passwordEncoder()); } //密码加密 @Bean public BCryptPasswordEncoder passwordEncoder(){ return new BCryptPasswordEncoder(); }}拦截规则
anyRequest:匹配所有请求路径access:SpringEl表达式结果为true时可以访问anonymous:匿名可以访问- `denyAll:用户不能访问
fullyAuthenticated:用户完全认证可以访问(非remember-me下自动登录)hasAnyAuthority:如果有参数,参数表示权限,则其中任何一个权限可以访问hasAnyRole:如果有参数,参数表示角色,则其中任何一个角色可以访问hasAuthority:如果有参数,参数表示权限,则其权限可以访问hasIpAddress:如果有参数,参数表示IP地址,如果用户IP和参数匹配,则可以访问hasRole:如果有参数,参数表示角色,则其角色可以访问permitAll:用户可以任意访问rememberMe:允许通过remember-me登录的用户访问authenticated:用户登录后可访问
认证失败处理类
/** * 返回未授权 */@Componentpublic class AuthenticationEntryPointImpl implements AuthenticationEntryPoint, Serializable { private static final long serialVersionUID = -8970718410437077606L; @Override public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException e) throws IOException { int code = HttpStatus.UNAUTHORIZED; String msg = "认证失败,无法访问系统资源,请先登陆"; ServletUtils.renderString(response, JSON.toJSONString(AjaxResult.error(code, msg))); }}认证流程
自定义认证过滤器
public class TokenLoginFilter extends UsernamePasswordAuthenticationFilter { private AuthenticationManager authenticationManager; private RsaKeyProperties prop; public TokenLoginFilter(AuthenticationManager authenticationManager, RsaKeyProperties prop) { this.authenticationManager = authenticationManager; this.prop = prop; } /** * @author cheetah * @description 登陆验证 * @date 2021/6/28 16:17 * @Param [request, response] * @return org.springframework.security.core.Authentication **/ public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException { try { UserPojo sysUser = new ObjectMapper().readValue(request.getInputStream(), UserPojo.class); UsernamePasswordAuthenticationToken authRequest = new UsernamePasswordAuthenticationToken(sysUser.getUsername(), sysUser.getPassword()); return authenticationManager.authenticate(authRequest); }catch (Exception e){ try { response.setContentType("application/json;charset=utf-8"); response.setStatus(HttpServletResponse.SC_UNAUTHORIZED); PrintWriter out = response.getWriter(); Map resultMap = new HashMap(); resultMap.put("code", HttpServletResponse.SC_UNAUTHORIZED); resultMap.put("msg", "用户名或密码错误!"); out.write(new ObjectMapper().writeValueAsString(resultMap)); out.flush(); out.close(); }catch (Exception outEx){ outEx.printStackTrace(); } throw new RuntimeException(e); } } /** * @author cheetah * @description 登陆成功回调 * @date 2021/6/28 16:17 * @Param [request, response, chain, authResult] * @return void **/ public void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException { UserPojo user = new UserPojo(); user.setUsername(authResult.getName()); user.setRoles((List<rolepojo>)authResult.getAuthorities()); //通过私钥进行加密:token有效期一天 String token = JwtUtils.generateTokenExpireInMinutes(user, prop.getPrivateKey(), 24 * 60); response.addHeader("Authorization", "Bearer "+token); try { response.setContentType("application/json;charset=utf-8"); response.setStatus(HttpServletResponse.SC_OK); PrintWriter out = response.getWriter(); Map resultMap = new HashMap(); resultMap.put("code", HttpServletResponse.SC_OK); resultMap.put("msg", "认证通过!"); resultMap.put("token", token); out.write(new ObjectMapper().writeValueAsString(resultMap)); out.flush(); out.close(); }catch (Exception outEx){ outEx.printStackTrace(); } }}流程
Security默认登录路径为/login,当我们调用该接口时,它会调用上边的attemptAuthentication方法;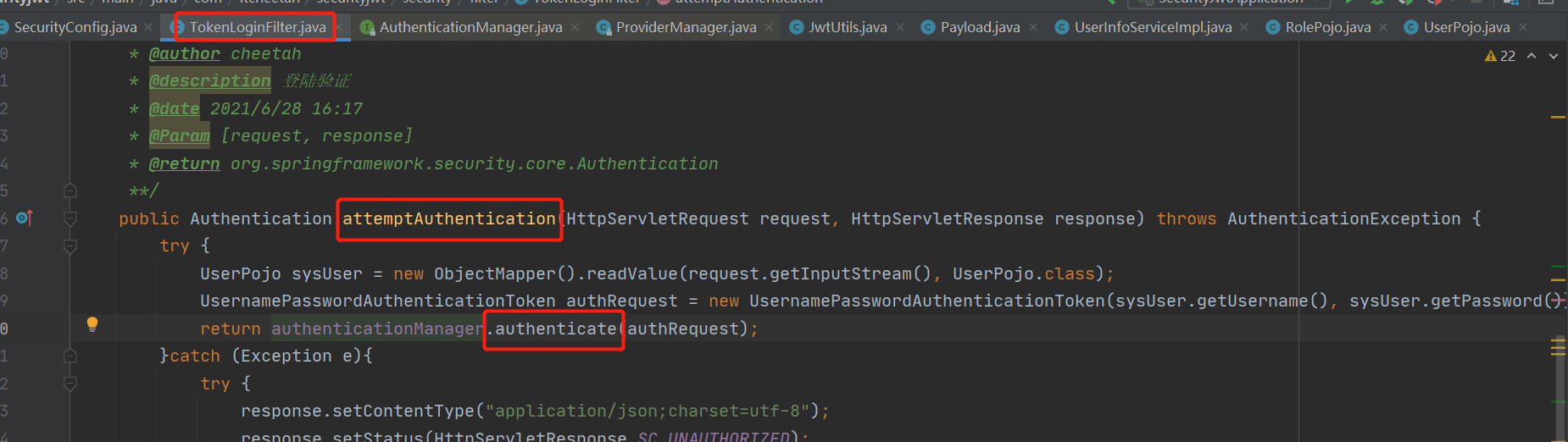
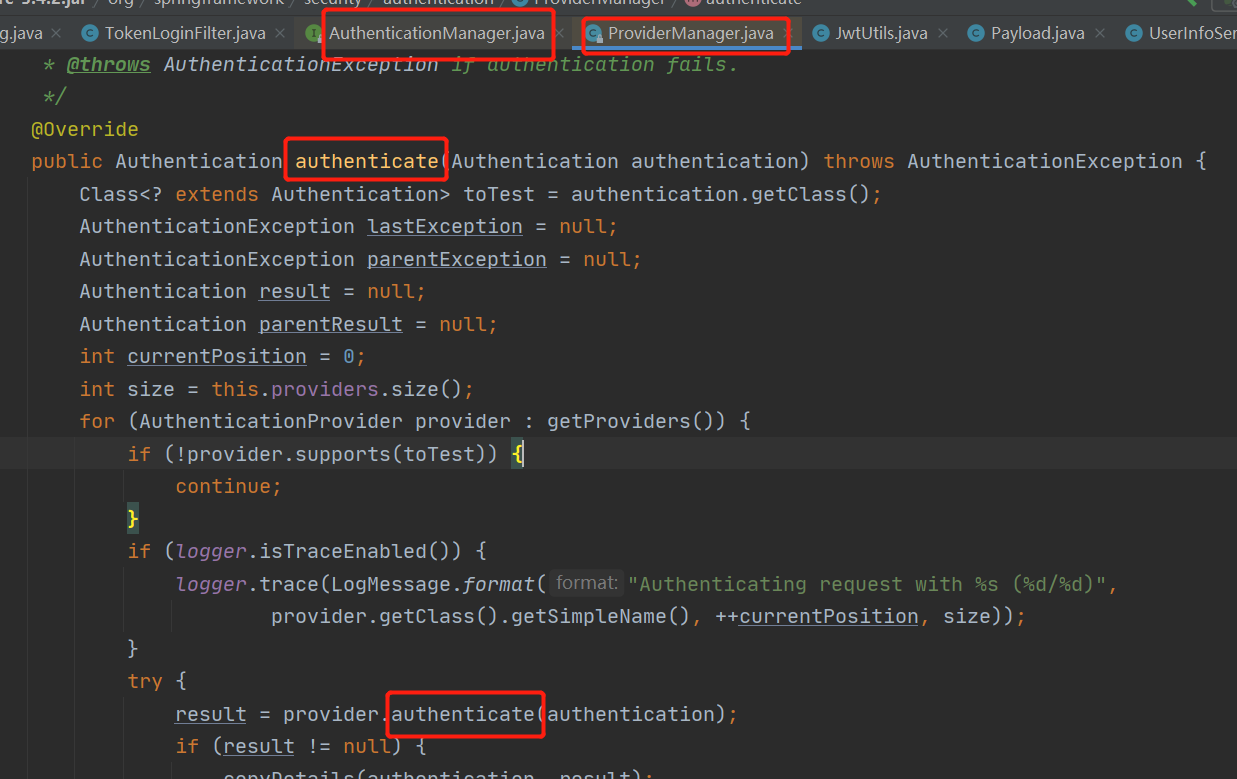
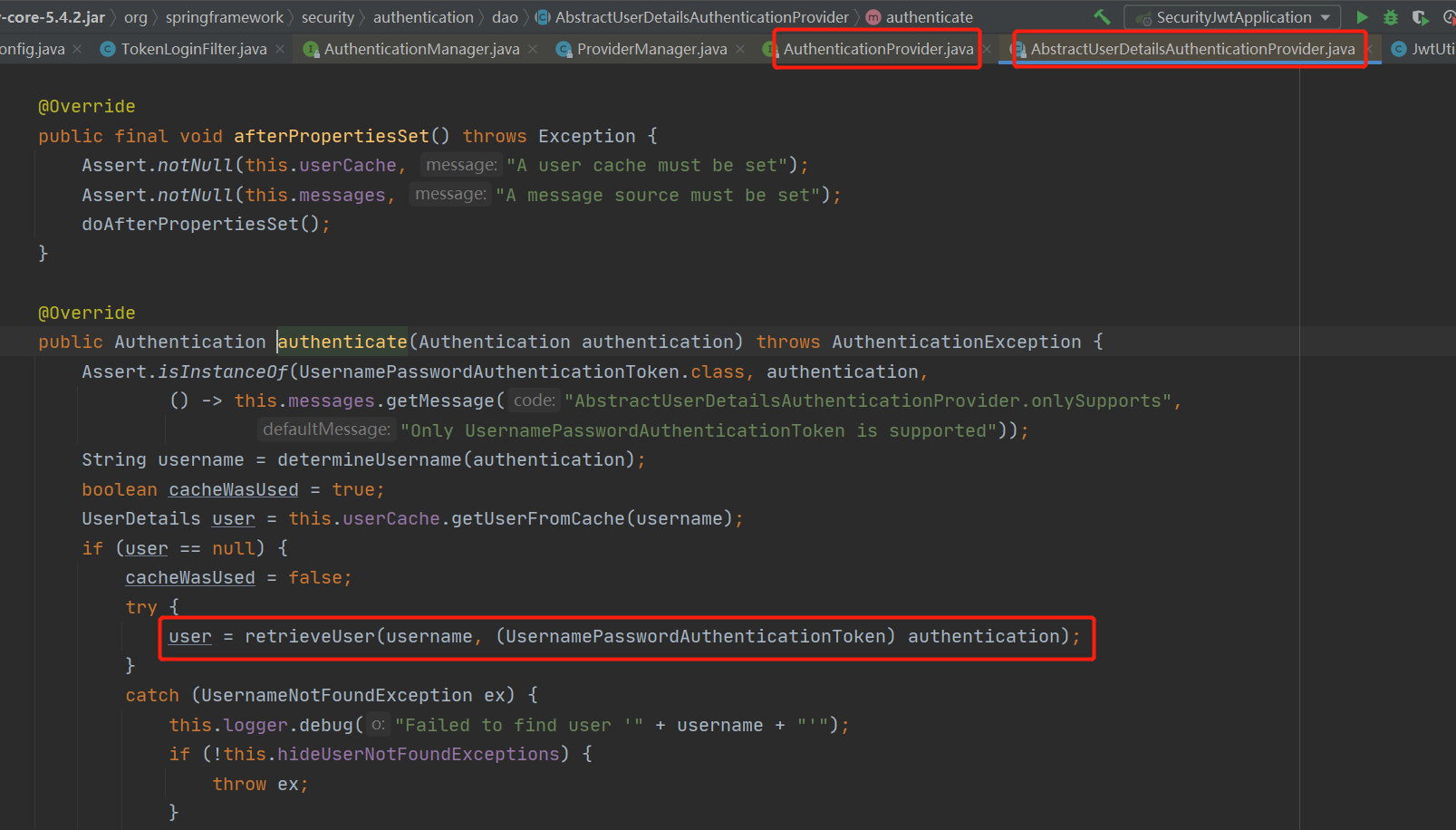
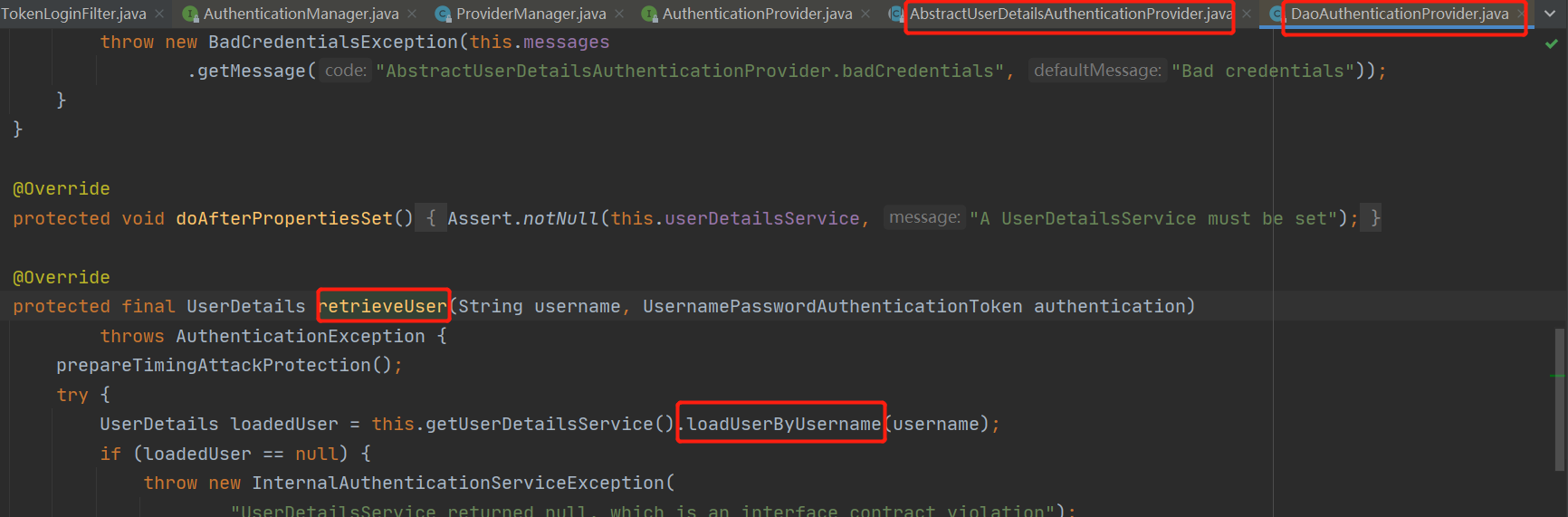
所以我们要自定......
原文转载:http://www.shaoqun.com/a/841206.html
跨境电商:https://www.ikjzd.com/
一淘网:https://www.ikjzd.com/w/1698
asiabill:https://www.ikjzd.com/w/1014
拍怕:https://www.ikjzd.com/w/2205
Goodmorning,everyone!之前我们已经说过用Shiro和JWT来实现身份认证和用户授权,今天我们再来说一下Security和JWT的组合拳。简介先赘述一下身份认证和用户授权:用户认证(Authentication):系统通过校验用户提供的用户名和密码来验证该用户是否为系统中的合法主体,即是否可以访问该系统;用户授权(Authorization):系统为用户分配不同的角色,以获取对应
必看!黑五网一热销爆款,还有这些利好政策:https://www.ikjzd.com/articles/112177
关于亚马逊广告运营,这三个层面的思考必不可少!:https://www.ikjzd.com/articles/112180
"价格战"一触即发,亚马逊最新改革被喷"变态"!:https://www.ikjzd.com/articles/112181
亚马逊反馈请求政策有什么变化?具体规则是什么?:https://www.ikjzd.com/articles/112182
口述:老婆被闺蜜洗脑后求我参与换妻:http://lady.shaoqun.com/a/70305.html
几位领导在办公室玩我 把她压在办公桌上进进出出:http://lady.shaoqun.com/a/247443.html
男人撕开奶罩揉吮奶头 我都说疼了他还在继续:http://lady.shaoqun.com/m/a/247840.html
口述强壮的公么征服我 公让我欲仙欲死3b:http://lady.shaoqun.com/m/a/247070.html
在武汉呆了50天,发现老公用了一袋草莓,把邻居哄睡着了!:http://lady.shaoqun.com/a/397666.html
23岁的男孩一大早就对着女邻居破口大骂:"小电影"让我欲火焚身:http://lady.shaoqun.com/a/397667.html
TikTok打开跨境卖家流量的新大门!:https://www.ikjzd.com/articles/146283
亚马逊和沃尔玛都瞄准的服饰赛道,欧美人表示:愿意买单!:https://www.ikjzd.com/articles/146275